20 Sep 2023
Jordan Harband, champion of the Get Intrinsics Proposal, joins us to iron out the SES strategy group’s position in advance of the plenary meeting in the coming week. We concluded that the proposal was good as-written because it satisfies the criteria: hidden intrinsics are distinguishable by parsing the first component of its name and checking whether a property exists on the global, and enumeration order places language intrinsics, the global object, and host intrinsics in order.
So, Repair Intrinsics for Hardened JavaScript can rely on the heuristic that all new undeniable intrinsics will be both before the global object and have no corresponding global, hardening such objects as they are revealed by language evolution.
So, Repair Intrinsics for Hardened JavaScript can rely on the heuristic that all new undeniable intrinsics will be both before the global object and have no corresponding global, hardening such objects as they are revealed by language evolution.
- 5 participants
- 39 minutes

5 Sep 2023
Daniel Minor reached out today to inform the champions of ShadowRealm of their intent to present a proposal to move ShadowRealm from stage 3 to 2 until the champions have an opportunity to complete the corresponding HTML integration proposal and to give the champions an opportunity to present an update to that effect instead. Participants on the call do not plan to present an update or present a counter-proposal, though Mark as a champion of ShadowRealm would prefer the proposal remain at Stage 3 but cannot promise HTML integration work in the near term.
- 3 participants
- 13 minutes

16 Aug 2023
We met again with Santiago Díaz to review and discuss mitigating data-only prototype-pollution-attacks in no-eval realms https://github.com/tc39/proposal-symbol-proto
- 4 participants
- 54 minutes

19 Jul 2023
Nicolò Ribaudo shared an update regarding the leakage of module scope over global scope for the Function constructor and indirect eval. TC-39 will be at liberty to fix the spec bug because the implementations are not consistent amongst themselves.
- 2 participants
- 3 minutes

23 Jun 2023
Today we met with Nicolò, a champion of deferred module exports to discuss potential reentrancy and plan interference hazards inherent to introducing deferred module exports. The proposal does not introduce a reentrance vector for the read barrier that triggers deferred evaluation since that occurs through property access and there is an expectation that this may cause reentrance already. But we begin to investigate a plan interference attack, for which we need a concrete example and will continue investigating next week.
- 4 participants
- 29 minutes

23 Jun 2023
Daniel Ehrenberg introduces us to Matthew Gaudet from Mozilla who is implementing ShadowRealm in SpiderMonkey who discusses challenges in integrating ShadowRealms with HTML, including reclassifying global objects, and various web APIs dependence on state rooted in the two extant types of global object: worker and window.
- 7 participants
- 56 minutes

2 Jun 2023
Santiago Díaz discusses Google’s proposal for mitigating data-only prototype-pollution-attacks.
In this meeting, Mark asked Santiago to use responsible disclosure for a possible case where Object.freeze does not maintain its invariants. Out-of-band, that investigation revealed a coding pattern that works as designed and does not violate any invariants: it is possible to overshadow a non-writable property up the prototype chain using definition semantics, but not assignment semantics. The frozen prototype does not change.
In this meeting, Mark asked Santiago to use responsible disclosure for a possible case where Object.freeze does not maintain its invariants. Out-of-band, that investigation revealed a coding pattern that works as designed and does not violate any invariants: it is possible to overshadow a non-writable property up the prototype chain using definition semantics, but not assignment semantics. The frozen prototype does not change.
- 5 participants
- 1:07 hours

8 May 2023
After a long hiatus, Guy Bedford updates Kris Kowal and attendees on the import attributes proposal (previously titled import reflection). This proposal continues to develop amicably with future proposals motivated by this group.
- 5 participants
- 45 minutes

26 Apr 2023
Minimum viable product to standardize the common parts of different module source formats (such as WASM, ESM) for Import Reflection, module expressions, and Compartments.
- 6 participants
- 50 minutes

13 Apr 2023
Discuss the relationship of CSP (Content Security Policy) with the compilation and instantiation of WASM and ESM Import Reflection.
- 4 participants
- 1:01 hours

10 Apr 2023
Import Reflection proposal has import source syntax to obtain compiled (uninstantiated) module source, such as a WebAssembly.Module. Discussion of its interaction with CSP, Module layering (née Compartment proposal), and SES shim.
- 7 participants
- 54 minutes

10 Apr 2023
Discussion of stage 0 proposal for Promise.ownProperties (or another name) to make Promise.all functionality more ergonomic. Suggestion for adding ModuleInstance.link to Layer 0, and subsequent discussion of the difference between reflection (provided in Layer 0) and virtualization (not provided in Layer 0).
- 7 participants
- 52 minutes

10 Apr 2023
Discussion of Shadow Realms globalThis, its prototype chain, and what host features are available by default. Unlike other Web realms, EventEmitter can be removed from the prototype, as can all ambient authority. Explanation of current state of Import Assertions proposal and how it may interact with SES.
- 5 participants
- 54 minutes

10 Apr 2023
Approaches for better support of object immutability: readonly ArrayBuffer and slices, superFreeze as the basis for transitive harden while working around the override mistake, and XS’s petrify.
- 6 participants
- 45 minutes
19 Jan 2023
Mathieu Hofman briefly updates us on the latest position from him and Mark regarding the acceptability of async disposal and we conclude our conversation with Justin Ridgewell regarding AsyncContext.
- 5 participants
- 41 minutes

17 Jan 2023
Discussion at friam led by Mark Miller.
This discussion is motivated by the proposal to add so-called "AsyncContext" to JavaScript. The question is how does this affect the safety of Hardened JS, the use of JavaScript as an object-capability language.
The discussion makes use of the examples at https://github.com/endojs/endo/pull/1424 . This PR will continue to evolve as our understanding does.
friam is a group of object-capability experts who have been meeting continually since the mid 1990s. This discussion examined the larger question of the safety of these mechanisms if added to ocap languages in general.
This discussion is motivated by the proposal to add so-called "AsyncContext" to JavaScript. The question is how does this affect the safety of Hardened JS, the use of JavaScript as an object-capability language.
The discussion makes use of the examples at https://github.com/endojs/endo/pull/1424 . This PR will continue to evolve as our understanding does.
friam is a group of object-capability experts who have been meeting continually since the mid 1990s. This discussion examined the larger question of the safety of these mechanisms if added to ocap languages in general.
- 10 participants
- 1:55 hours

11 Jan 2023
Mark S. Miller (MarkM) did another deep dive into his investigation of the security properties of AsyncContext and the champion of that proposal, Justin Ridgewell of Vercel, was able to join us. There will be a Part III.
- 4 participants
- 1:01 hours

4 Jan 2023
Mark Miller lays out the groundwork for an explanation of his investigation into the security of AsyncContext.
- 6 participants
- 53 minutes

22 Dec 2022
Caridy Patiño and Kris Kowal investigate a lower-level design for virtual module sources using what we might call a contour controller, an object that stands for a module record and controls its linkage and bindings, presumably imperatively.
- 4 participants
- 29 minutes

15 Dec 2022
Today we discussed our advice to the HTML standard for desirable ways to allow programs to trap exceptions and rejections in a shadow realm.
- 3 participants
- 41 minutes

7 Dec 2022
Wherein we review the feedback we received for Mass Proxy Revocation, Module Harmony, and ShadowRealms.
- 6 participants
- 52 minutes

9 Nov 2022
Wherein we discuss Yulia Startsev’s most recent change to the proposal for synchronous deferred execution of modules, wherein the read barrier is delimited on property access and does not exist for module lexical bindings. We begin to consider the possibility of programs that are correct in isolation and broken in composition with this feature.
- 5 participants
- 58 minutes

19 Oct 2022
Today, Scott Miles joins us from ArcJS to talk through their implementation and Alex Vincent does a run-through of his intended presentation for TC39 on Proxy mass revocation.
- 4 participants
- 46 minutes

13 Oct 2022
Wherein we meet the Google ArcsJS team, who use the ses Hardened JavaScript as a foundation for mitigating user fingerprinting.
- 9 participants
- 1:03 hours

28 Sep 2022
In this session, we review a change proposed by Aaron Davis that replaces the scope proxy leak in SES with a sloppy mode leak that affects functions declared in the global scope of a strict script evaluated by the SES shim.
- 4 participants
- 47 minutes

21 Sep 2022
Wherein we discuss Caridy’s PR #78 that introduces a module handler object / options bag.
https://github.com/tc39/proposal-compartments/pull/78
https://github.com/tc39/proposal-compartments/pull/78
- 4 participants
- 56 minutes

7 Sep 2022
Peter Hoddie updates us on some thoughts about records and tuples and a desire to pursue a rigorous approach to immutability for objects in general. Leo reviews slides for the ShadowRealm update for next week’s plenary.
- 5 participants
- 52 minutes

31 Aug 2022
Daniel Ehrenberg joins us to inquire about our thoughts on deep equality as a language feature and we discuss prose for eliding stack traces when they pass through the callable boundary of shadow realms.
- 6 participants
- 48 minutes

24 Aug 2022
Alex presents a draft of mass revocation of proxies and Jack Works proposes a higher fidelity module source virtualization, capable of emulating initialization of hoisted functions.
- 5 participants
- 51 minutes

17 Aug 2022
Wherein we discuss the pedagogy of the Module and importHook interfaces and the possible need for an arguments bag.
- 4 participants
- 48 minutes

11 Aug 2022
* What to do with import.meta.resolve
* Nested module blocks and combinations of module blocks and instances.
* Module constructor signature beyond Module(source, specifier, …) for importHook, importMeta, and beyond to account for import assertions.
** Resolution: tentative signature is new Module(source, importHook, referrer?, {meta?}?)
* Nested module blocks and combinations of module blocks and instances.
* Module constructor signature beyond Module(source, specifier, …) for importHook, importMeta, and beyond to account for import assertions.
** Resolution: tentative signature is new Module(source, importHook, referrer?, {meta?}?)
- 5 participants
- 49 minutes

3 Aug 2022
Wherein Caridy shows us how well layering module blocks on first-class modules works out, and we discuss _at length_ how import.meta interacts between first-class modules, module blocks, and direct eval.
- 3 participants
- 55 minutes

29 Jun 2022
Wherein we discuss stage 1 governance among champions for the compartments proposal, the status of the proposal, pending pull requests, and possible future direction.
- 3 participants
- 54 minutes

22 Jun 2022
This week we met with Guy Bedford to identify the intersection between import reflection and compartments.
- 5 participants
- 42 minutes

25 May 2022
Jack Works brings questions about the proposed update for the compartment API and Mathieu brings questions about errors thrown from shadow realms.
- 4 participants
- 54 minutes

18 May 2022
Wherein we welcome Olaf of MetaMask’s Snaps team to discuss StaticModuleRecord security claims, and then review Kris’s refresh of the TC39 Compartment proposal diff.
- 5 participants
- 57 minutes

11 May 2022
Wherein we discuss reentrancy hazards of Promise.resolve(x) that motivate the need for a promise brand check, the hazards of a Promise brand check, and how to mitigate them.
- 3 participants
- 56 minutes

4 May 2022
Wherein ZB from MetaMask/Consensys and Peter and Patrick from Moddable meet to discuss options for the timing of the importMetaHook and also how to overload the module descriptor object.
- 4 participants
- 48 minutes

27 Apr 2022
Mathieu presents an idea of how to overcome the property override mistake.
- 4 participants
- 54 minutes

20 Apr 2022
Leo provides an update on the consensus position for document.all interaction with ShadowRealm, which is to pursue the status quo.
- 3 participants
- 12 minutes

6 Apr 2022
Mathieu shares progress on symbols as weakmap keys and Leo and Rick share performance figures for near membranes.
- 6 participants
- 50 minutes

23 Mar 2022
Wherein Caridy leads a conversation about what to do about error and rejection events.
- 3 participants
- 24 minutes

9 Mar 2022
Nicoló Ribaudo of Babel gives us some help improving SES’s use of Babel.
- 5 participants
- 36 minutes

9 Mar 2022
Wherein Leo proposes a graduated plan to add serialization at the ShadowRealm boundary.
- 4 participants
- 23 minutes

17 Feb 2022
Kris gives a presentation on the agreement and open questions for the Compartment proposal as XS’s native implementation of dynamic module loading converges with the SES shim.
- 4 participants
- 57 minutes

12 Feb 2022
We discuss mechanisms for enumerating hidden intrinsics and the “petrification” of object graphs.
- 6 participants
- 46 minutes

19 Jan 2022
This week we discuss Alex Vincent’s proposal for mass proxy revocation, including Bradley Farias’s development on that proposal using revocation controller and signal pairs.
- 7 participants
- 53 minutes

5 Jan 2022
This week we reviewed the arguments for and against symbols as weakmap keys and began a conversation about bulk revocation of proxies.
- 7 participants
- 50 minutes

17 Nov 2021
This week we discuss two topics of ShadowRealm, how to represent wrapped functions, particularly their name and length, and opine on a future proposal to allow SharedArrayBuffers to transit between shadow realms.
- 4 participants
- 51 minutes

30 Sep 2021
In this call, MarkM and Mathieu deliver a new understanding about how Records and Tuples should be new language primitives, how this will interact with the evolution of SES to accommodate them, and the constraints on the design that are sufficient to preserve confinement invariants.
- 6 participants
- 56 minutes

23 Sep 2021
In this conversation, we explore a holistic approach to rooting out how bad each of the options for Records and Tuples are for breaking existing code.
- 11 participants
- 58 minutes

15 Sep 2021
Wherein we discuss whether typeof should produce "object" or ("record" or "tuple") and the design tensions of supporting Boxes.
- 9 participants
- 1:02 hours

18 Aug 2021
Mathieu Hofman and Daniel Ehrenberg lead a discussion on Boxes and their design trade-offs.
- 5 participants
- 1:15 hours

11 Aug 2021
Mathieu Hofman shares a chain of complications to boxes within records and tuples that force a design decision between a memory leak hazard and a correctness hazard for existing code.
- 7 participants
- 54 minutes

28 Jul 2021
Continuation of R&T/Box discussion (moved from 2021-07-28)
Regarding Node.js relaxing its code contribution guidelines around defense against mutation to intrinsics, at the expense of 10% performance and a considerably higher bar for contributors. We conclude that we might be able to make direct use of intrinsics more ergonomic while addressing the concern of safely discovering original intrinsics.
Continued conversation about naming Realms. We arrive at the idea of pairing a taxonomic name with a behavioral name, like ModuleGlobe (née Compartment), IntrinsicsSystem, SharedUniverse, ProcessMultiverse, &c.
Regarding Node.js relaxing its code contribution guidelines around defense against mutation to intrinsics, at the expense of 10% performance and a considerably higher bar for contributors. We conclude that we might be able to make direct use of intrinsics more ergonomic while addressing the concern of safely discovering original intrinsics.
Continued conversation about naming Realms. We arrive at the idea of pairing a taxonomic name with a behavioral name, like ModuleGlobe (née Compartment), IntrinsicsSystem, SharedUniverse, ProcessMultiverse, &c.
- 7 participants
- 55 minutes

21 Jul 2021
TC-39 advanced Realms to Stage 3. They liked everything but the color.
- 7 participants
- 55 minutes

30 Jun 2021
Robin Ricard leads a discussion about Records and Tuples and a potential interaction with Realms. Debate continues to weigh two possible directions for the proposal to make progress past security and complexity obstacles.
- 6 participants
- 59 minutes

23 Jun 2021
This session had a short quorum. We deferred the topic of Records and Tuples a week and Alex Vincent posted a call for contributors for new promise combinators.
- 4 participants
- 8 minutes

22 Jun 2021
Dan Clark visits to talk about import assertions and enforcing a limited set of module types. Jordan Harband visits to discuss Realms progress.
- 8 participants
- 57 minutes

9 Jun 2021
This week, Alex discussed his idea to add Promise.allProperties to the language, concluding that a Promise.allEntries might be a suitably general foundation for shallow object and Map resolution. We discussed invariants that the language must or should preserve to avoid introducing zero-day exploits to lockdown shims in the wild.
- 6 participants
- 36 minutes

2 Jun 2021
Realms attempted an advance to Stage 6 at TC-39 Plenary the prior week. In this meeting we debrief and discuss next steps toward advancing that proposal, including an important relaxation of the prohibition against host extensions, IO, or mutation side-effects provided that these can extensions can continue to be erased by the SES shim, in anticipation of a future Lockdown proposal.
- 5 participants
- 39 minutes

19 May 2021
Leo Balter discusses options to present to TC-39 the following week toward asking for Stage 3 advancement.
- 7 participants
- 55 minutes

19 May 2021
We discussed with Daniel Ehrenberg the landscape for progress on records and tuples, reviewed the branches of the problem, and how each option introduces a new hazard for old code, but should not break any existing usage.
- 5 participants
- 34 minutes

5 May 2021
Leo Balter discusses Realms topics needed to build consensus for Stage 3.
- 7 participants
- 49 minutes

5 May 2021
Caridy Patiño demonstrates a proof of concept for transparent membranes between isolated realms.
- 3 participants
- 51 minutes

7 Apr 2021
We discussed Leo’s proposal for an API oriented around just code evaluation and a function wrapper, in response to Daniel’s API proposal oriented around connect, in an effort to close an intuition gap among the API’s end users at Salesforce.
- 4 participants
- 46 minutes

7 Apr 2021
Alex Vincent led a discussion about a design challenge for multi-facet membranes and we also briefly discussed module fragments with Daniel Ehrenberg.
- 6 participants
- 52 minutes

7 Apr 2021
Viability Records and Tuples for Stage 3 with Daniel Ehrenberg and champions of Records and Tuples. MarkM brings a concern regarding -0, which the champions address. A concern remains about the coherence of the language, given that some of the goals of tuples and records as suitable as keys in maps and values in sets might be achievable with other means that preserve amortized constant time comparison.
Upcoming changes to Node Policies due to Import Maps (5min) with Bradley Farias. Node.js will allow an escape hatch in policies that will open up ambient authority to import maps. Module specifiers will be eagerly canonicalized into the domain of fully qualified URL or something else that looks like a path relative URL but must not begin with . or .. path components.
Isolated Realms, new API Review with Caridy and Leo.
Upcoming changes to Node Policies due to Import Maps (5min) with Bradley Farias. Node.js will allow an escape hatch in policies that will open up ambient authority to import maps. Module specifiers will be eagerly canonicalized into the domain of fully qualified URL or something else that looks like a path relative URL but must not begin with . or .. path components.
Isolated Realms, new API Review with Caridy and Leo.
- 9 participants
- 54 minutes

22 Jan 2021
Wherein we discuss Daniel Ehrenberg’s draft proposal for web bundles.
- 5 participants
- 58 minutes

12 Jan 2021
Alex Vincent presents an early draft presentation on JavaScript membranes.
- 2 participants
- 41 minutes

2 Dec 2020
Fred Schott (Snowpack) and Jovi de Croock (Preact) join the SES community to discuss language support for hot module replacement.
- 6 participants
- 1:08 hours

25 Nov 2020
Daniel Ehrenberg joins the SES community to discuss Surma’s TC39 proposal for JavaScript module blocks and how they relate to the SES Compartments proposal.
- 5 participants
- 51 minutes

4 Nov 2020
Kris Kowal presents recommendations for the TC39 Compartment module loader proposal, like a constructor options bag.
- 5 participants
- 51 minutes

24 Apr 2020
Michael FIG led a naming discussion for the eventual-send proposal. Alex Vincent proposed that instead of having a separate constructor, we could create a maker static function on the Promise object that returns a Promise. Saleh proposed the maker function might use the root “delegate” to disassociate the term from handled vs unhandled promise rejections. We agreed to avoid the term proxy on the grounds that, while we borrow the handler pattern from the proxy constructor, the handler itself is not sufficiently similar to a proxy handler to suggest they’re related. By the end of the discussion, we had loose consensus that these names were consistent and good:
* Promise.delegate(handler) returns a “delegated promise” and is analogous to Proxy.revocable, Array.from, or Object.fromEntries, in that it is a static method of a constructor that returns an object of the same type as the constructor.
* Promise.get(promise, prop), Promise.apply(promise, …), Promise.applyMethod(promise, prop, …) all could be static methods of the Promise and that we’ll consider alternatives.
* No changes to the names “presence” and “remotable”.
https://github.com/tc39/proposal-eventual-send/issues/11#issuecomment-618711001
We reviewed Caridy’s proposal for Realms to the “incubator” scheduled for the 27th. We attempted to isolate and address the two major concerns brought up in discussion with members of the committee previously, regarding layering the DOM atop realms and “consistency with the principles of the web”.
Kris updated the group with progress on the Compartment shim. We are beginning to add support for Compartment modules. We may eventually need to extend Compartments to support inter-linkage with modules not defined with JavaScript text, like WASM.
* Promise.delegate(handler) returns a “delegated promise” and is analogous to Proxy.revocable, Array.from, or Object.fromEntries, in that it is a static method of a constructor that returns an object of the same type as the constructor.
* Promise.get(promise, prop), Promise.apply(promise, …), Promise.applyMethod(promise, prop, …) all could be static methods of the Promise and that we’ll consider alternatives.
* No changes to the names “presence” and “remotable”.
https://github.com/tc39/proposal-eventual-send/issues/11#issuecomment-618711001
We reviewed Caridy’s proposal for Realms to the “incubator” scheduled for the 27th. We attempted to isolate and address the two major concerns brought up in discussion with members of the committee previously, regarding layering the DOM atop realms and “consistency with the principles of the web”.
Kris updated the group with progress on the Compartment shim. We are beginning to add support for Compartment modules. We may eventually need to extend Compartments to support inter-linkage with modules not defined with JavaScript text, like WASM.
- 7 participants
- 1:28 hours
2 Aug 2019
The tc39 SES Status Update presentation by itself is at
https://www.youtube.com/watch?v=A943wrmLJv0&list=PLzDw4TTug5O1jzKodRDp3qec8zl88oxGd
https://www.youtube.com/watch?v=A943wrmLJv0&list=PLzDw4TTug5O1jzKodRDp3qec8zl88oxGd
- 4 participants
- 1:47 hours

2 Aug 2019
The "SES Status Update" presentation I originally gave at the July 2019 tc39 meeting I gave again to the SES-mtg on Aug 1, and recorded.
"SES Status Update" as originally presented at tc39 at
https://www.youtube.com/watch?v=cspzkRvs1Ig
Starts at the fourth slide because I forgot to turn recording on earlier.
Full Aug1 SES mtg at
https://www.youtube.com/watch?v=IxwX200g4TI&list=PLzDw4TTug5O1jzKodRDp3qec8zl88oxGd
"SES Status Update" as originally presented at tc39 at
https://www.youtube.com/watch?v=cspzkRvs1Ig
Starts at the fourth slide because I forgot to turn recording on earlier.
Full Aug1 SES mtg at
https://www.youtube.com/watch?v=IxwX200g4TI&list=PLzDw4TTug5O1jzKodRDp3qec8zl88oxGd
- 2 participants
- 40 minutes

10 Mar 2019
Content begins at 5:45
Before that is mostly figuring out how to use Zoom
Before that is mostly figuring out how to use Zoom
- 4 participants
- 1:40 hours
24 Jan 2019
Recorded from the "SES Strategy" meeting on Jan 24, 2019.
Caja consisted of two main parts: Domado, for securing/virtualizing the browser APIs, and SES, for securing JavaScript. Securing the html4 browser API and ES3 were both horrendously difficult. Changes to JavaScript made securing it easy. Changes to the browser have only made the Domado problem worse. What could be changed about the browser to make Domado-level security easy?
Caja consisted of two main parts: Domado, for securing/virtualizing the browser APIs, and SES, for securing JavaScript. Securing the html4 browser API and ES3 were both horrendously difficult. Changes to JavaScript made securing it easy. Changes to the browser have only made the Domado problem worse. What could be changed about the browser to make Domado-level security easy?
- 5 participants
- 1:35 hours

24 Jan 2019
Recorded at the "SES Strategy Meeting" on Jan 24, 2019. See https://github.com/erights/PNLSOWNSF/blob/master/PrivateName.js
Bradley observed that a class decorator can obtain the source of the class, rewrite it, evaluate that, and replace the original class with the result. This means there's no loss of security providing a class decorator with access to the internal PrivateName.
However, the decorator can only do an indirect eval. It cannot access the lexical scope that the class appears in. Thus, a "private" declaration that appears outside the class remains protected.
Bradley observed that a class decorator can obtain the source of the class, rewrite it, evaluate that, and replace the original class with the result. This means there's no loss of security providing a class decorator with access to the internal PrivateName.
However, the decorator can only do an indirect eval. It cannot access the lexical scope that the class appears in. Thus, a "private" declaration that appears outside the class remains protected.
- 2 participants
- 33 minutes
22 Jan 2019
Recorded from the "Frozen Realms shim collaboration" meeting on Jan 22, 2019. See https://github.com/katelynsills/legacy-todo/blob/master/manifest.json
Unfortunately, we accidentally started recording well after this discussion started.
We discussed how the policy decisions expressing what authority should be provided to packages are expressed, who makes those policy decisions, and what the workflow is to make a new policy decision --- or raise an alarm --- when a new version demands more authority.
Resolution:
From outside an application, express and enforce policy on what authority is provided to an application as a whole. We call this the "aggregate authority", as it is aggregated over all packages that comprise the application.
The https://github.com/katelynsills/legacy-todo/blob/master/manifest.json is an example of an application's internal expression and enforcement of policy about how the authority provided to the application as a whole is to be further subdivided and attenuated among the individual packages that comprise the application.
Example: The outside policy may express that the "fs" module that the application as a whole sees is attenuated to providing access to example/*, whereas the application layers on this a further attenuated to provide a particular package with access only to example/log.txt
Unfortunately, we accidentally started recording well after this discussion started.
We discussed how the policy decisions expressing what authority should be provided to packages are expressed, who makes those policy decisions, and what the workflow is to make a new policy decision --- or raise an alarm --- when a new version demands more authority.
Resolution:
From outside an application, express and enforce policy on what authority is provided to an application as a whole. We call this the "aggregate authority", as it is aggregated over all packages that comprise the application.
The https://github.com/katelynsills/legacy-todo/blob/master/manifest.json is an example of an application's internal expression and enforcement of policy about how the authority provided to the application as a whole is to be further subdivided and attenuated among the individual packages that comprise the application.
Example: The outside policy may express that the "fs" module that the application as a whole sees is attenuated to providing access to example/*, whereas the application layers on this a further attenuated to provide a particular package with access only to example/log.txt
- 5 participants
- 57 minutes
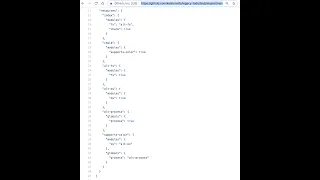
22 Jan 2019
Recorded from the "Frozen Realms shim collaboration" meeting on Jan 22, 2019. See https://github.com/agoric/ses
Brian Warner walks us through how to install and use the current SES shim. This version of the SES shim directly supports safe evaluators for evaluating strings, but does not yet support safe module loading. We also discuss various packager alternatives for packaging modules as evaluable strings.
Brian Warner walks us through how to install and use the current SES shim. This version of the SES shim directly supports safe evaluators for evaluating strings, but does not yet support safe module loading. We also discuss various packager alternatives for packaging modules as evaluable strings.
- 6 participants
- 1:07 hours