17 Nov 2019
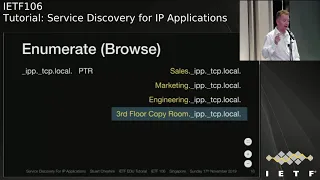
Service Discovery for IP Applications
This tutorial covers the three fundamental operations of DNS-based service discovery: Offer, Enumerate, and Use. It includes the APIs available on multiple platforms to access these operations along with both local service discovery using Multicast DNS and wide area service discovery using conventional unicast DNS.
Slides at:
https://datatracker.ietf.org/meeting/106/materials/slides-106-edu-sessf-service-discovery-for-ip-applications-00
TUTORIALIP meeting session at IETF106
2019/11/17 1345
https://datatracker.ietf.org/meeting/106/proceedings/
This tutorial covers the three fundamental operations of DNS-based service discovery: Offer, Enumerate, and Use. It includes the APIs available on multiple platforms to access these operations along with both local service discovery using Multicast DNS and wide area service discovery using conventional unicast DNS.
Slides at:
https://datatracker.ietf.org/meeting/106/materials/slides-106-edu-sessf-service-discovery-for-ip-applications-00
TUTORIALIP meeting session at IETF106
2019/11/17 1345
https://datatracker.ietf.org/meeting/106/proceedings/
- 3 participants
- 1:04 hours
7 Nov 2018
Trusted Execution Environment Protocol
This talk explains the concept of TrustZone (as one example of a widely deployed technology offering sandboxing) and the Open Trust Protocol.
Chips used on smart phones, tablets, and many consumer appliances today have built-in support for a so-called Trusted Execution Environment (TEE). The Tis a security concept that separates normal operating systems, like Linux, from code that requires higher security protection, like security-related code. The underlying idea of this sandboxing approach is to have a smaller codebase that is better reviewed and test and to provide it with more rights. They run on the so-called Secure World (in comparison to the Linux operating system that would run in the Normal World).
TEEs have been on the market for a while and have been successfully used for a number of applications, such as payment. However, the technology hasn't reached its full potential the market is quite fragmented with vendors offering a larger number of real-time operating systems running in a TEE.
With the Open Trust Protocol we have been trying to develop an application layer security protocol that allows the management (install, update, delete) of trusted applications running on the TEE.
https://datatracker.ietf.org/meeting/99/materials/slides-99-edu-sessi-trusted-execution-environments-tee-and-the-open-trust-protocol-otrp-01
This talk explains the concept of TrustZone (as one example of a widely deployed technology offering sandboxing) and the Open Trust Protocol.
Chips used on smart phones, tablets, and many consumer appliances today have built-in support for a so-called Trusted Execution Environment (TEE). The Tis a security concept that separates normal operating systems, like Linux, from code that requires higher security protection, like security-related code. The underlying idea of this sandboxing approach is to have a smaller codebase that is better reviewed and test and to provide it with more rights. They run on the so-called Secure World (in comparison to the Linux operating system that would run in the Normal World).
TEEs have been on the market for a while and have been successfully used for a number of applications, such as payment. However, the technology hasn't reached its full potential the market is quite fragmented with vendors offering a larger number of real-time operating systems running in a TEE.
With the Open Trust Protocol we have been trying to develop an application layer security protocol that allows the management (install, update, delete) of trusted applications running on the TEE.
https://datatracker.ietf.org/meeting/99/materials/slides-99-edu-sessi-trusted-execution-environments-tee-and-the-open-trust-protocol-otrp-01
- 20 participants
- 2:02 hours
4 Nov 2018
Traffic Engineering in the IETF
Traffic Engineering is now so important as a glue for the Internet that it's worth stepping back to consider what it is, how it works, and what work the IETF is currently engaged in.
This tutorial introduces the concept of Traffic Engineering (TE), describes the basic techniques, runs through the key TE technologies that have been developed in the IETF, and provides pointers to current IETF efforts to enhance Traffic Engineering. Presented at IETF 103, the talk describes recent architectural models such as the Architecture for Application Based Network Operation (ABNO), PCE as a Central Controller (PCE-CC), and a Framework for Abstraction and Control of TE Networks (ACTN), and it mentions new approaches to Traffic Engineering delivered by Segment Routing (SR) and Deterministic Networking (DetNet). It also preview the work on YANG models for the control of TE resources and virtual networks.
Slides at: https://datatracker.ietf.org/meeting/103/materials/slides-103-edu-sessk-an-ietf-traffic-engineering-overview-01
Traffic Engineering is now so important as a glue for the Internet that it's worth stepping back to consider what it is, how it works, and what work the IETF is currently engaged in.
This tutorial introduces the concept of Traffic Engineering (TE), describes the basic techniques, runs through the key TE technologies that have been developed in the IETF, and provides pointers to current IETF efforts to enhance Traffic Engineering. Presented at IETF 103, the talk describes recent architectural models such as the Architecture for Application Based Network Operation (ABNO), PCE as a Central Controller (PCE-CC), and a Framework for Abstraction and Control of TE Networks (ACTN), and it mentions new approaches to Traffic Engineering delivered by Segment Routing (SR) and Deterministic Networking (DetNet). It also preview the work on YANG models for the control of TE resources and virtual networks.
Slides at: https://datatracker.ietf.org/meeting/103/materials/slides-103-edu-sessk-an-ietf-traffic-engineering-overview-01
- 3 participants
- 1:03 hours
15 Jul 2018
Identifier Locator Network Protocol
This talk provides an introduction & overview of the Identifier-Locator Networking Protocol (ILNP), focusing on ILNP as a superset of IPv6.
The core idea behind ILNP has its roots in the "8+8” naming architecture of
the early 1990s, and discussions within the IRTF Name Space Research Group (NSRG), circa 1999-2002. ILNP is defined as an IRTF Experimental protocol in RFC 6740 to RFC 6748, and supported by ongoing research from lab results based on running code. This talk will cover the key architectural concepts of ILNP and also the specific design & operation of ILNP as a superset of IPv6, with examples of how ILNP implements mobility. More information is available at the ILNP website.
Slides from presentation:
https://datatracker.ietf.org/meeting/102/materials/slides-102-edu-sessg-an-introduction-to-the-identifier-locator-network-protocol-ilnp-00
ILNP meeting session at IETF102
2018/07/15 1345
https://datatracker.ietf.org/meeting/102/proceedings/
This talk provides an introduction & overview of the Identifier-Locator Networking Protocol (ILNP), focusing on ILNP as a superset of IPv6.
The core idea behind ILNP has its roots in the "8+8” naming architecture of
the early 1990s, and discussions within the IRTF Name Space Research Group (NSRG), circa 1999-2002. ILNP is defined as an IRTF Experimental protocol in RFC 6740 to RFC 6748, and supported by ongoing research from lab results based on running code. This talk will cover the key architectural concepts of ILNP and also the specific design & operation of ILNP as a superset of IPv6, with examples of how ILNP implements mobility. More information is available at the ILNP website.
Slides from presentation:
https://datatracker.ietf.org/meeting/102/materials/slides-102-edu-sessg-an-introduction-to-the-identifier-locator-network-protocol-ilnp-00
ILNP meeting session at IETF102
2018/07/15 1345
https://datatracker.ietf.org/meeting/102/proceedings/
- 12 participants
- 1:07 hours

12 Nov 2017
WebRTC, Web Real-Time Communications, is revolutionizing the way web users communicate, both in the consumer and enterprise worlds.
WebRTC adds standard APIs and built-in real-time audio and video capabilities and codecs to browsers without a plug-in. With just a few lines of JavaScript, web developers can add high quality peer-to-peer voice, video, and data channel communications to their collaboration, conferencing, telephony, or even gaming site or application.
Slides from presentation at:
https://datatracker.ietf.org/meeting/100/materials/slides-100-edu-sessm-webrtc-tutorial-part-1-00
WebRTC adds standard APIs and built-in real-time audio and video capabilities and codecs to browsers without a plug-in. With just a few lines of JavaScript, web developers can add high quality peer-to-peer voice, video, and data channel communications to their collaboration, conferencing, telephony, or even gaming site or application.
Slides from presentation at:
https://datatracker.ietf.org/meeting/100/materials/slides-100-edu-sessm-webrtc-tutorial-part-1-00
- 3 participants
- 45 minutes

16 Jul 2017
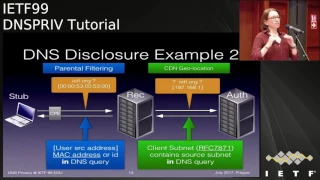
DNS Privacy
This talk discusses the various ways DNS queries are exposed to leakage and surveillance, what has been designed and implemented, and where we are going next.
DNS is one of the oldest pieces of protocol "Infrastructure" used in the Internet, and the most widely used. Confidentiality or privacy of users' DNS queries and responses was not included in its design. TheDNS PRIVate Exchange was created to design a mechanism to add a layer of confidentiality to DNS queries, without adversely impacting the existing DNS protocol or the user base.
Slides from the presentation:
https://datatracker.ietf.org/meeting/99/materials/slides-99-edu-sessh-dns-privacy-tutorial-00
DNSPRIV TUTORIAL at IETF99
2017/07/16 1230
https://datatracker.ietf.org/meeting/99/proceedings/
This talk discusses the various ways DNS queries are exposed to leakage and surveillance, what has been designed and implemented, and where we are going next.
DNS is one of the oldest pieces of protocol "Infrastructure" used in the Internet, and the most widely used. Confidentiality or privacy of users' DNS queries and responses was not included in its design. TheDNS PRIVate Exchange was created to design a mechanism to add a layer of confidentiality to DNS queries, without adversely impacting the existing DNS protocol or the user base.
Slides from the presentation:
https://datatracker.ietf.org/meeting/99/materials/slides-99-edu-sessh-dns-privacy-tutorial-00
DNSPRIV TUTORIAL at IETF99
2017/07/16 1230
https://datatracker.ietf.org/meeting/99/proceedings/
- 5 participants
- 1:04 hours